Phishing Attacks in 2025: A Persistent Enterprise Threat
In 2025, phishing attacks remain a major security challenge for enterprises. As attackers increasingly adopt identity-based techniques rather than exploiting software vulnerabilities, phishing poses an even greater threat than before. Today, phishing toolkits capable of bypassing multi-factor authentication (MFA) have become commonplace, able to steal accounts protected by SMS codes, one-time passwords (OTP), and push-based verification. As preventive measures fail, detection systems are under continuous pressure.
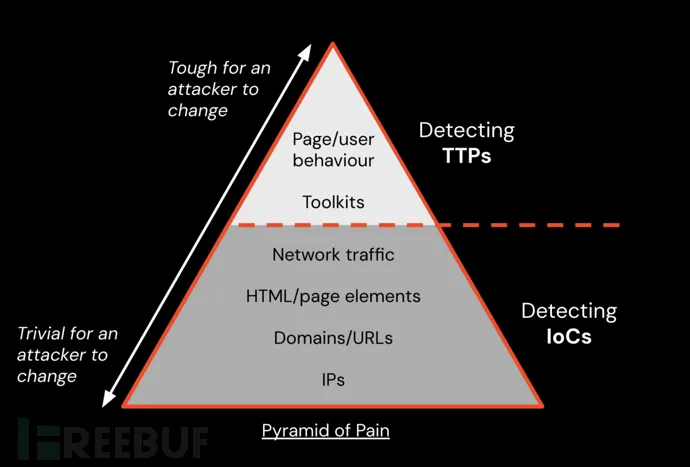
The fundamental dilemma of phishing detection lies in this: relying on commonly used Indicators of Compromise (IoCs) to identify phishing pages is increasingly ineffective because almost every phishing attack uses a unique combination of domain names, URLs, IP addresses, page structures, and targeted applications. In essence, every phishing attack is “zero-day” — a chilling reality.
This article does not intend to exaggerate the threat, but to expose the inherent flaws in current detection mechanisms. If every phishing attempt resembles a zero-day attack, it indicates that our detection approach is fundamentally broken.
Fundamentals of Phishing Detection
A typical phishing attack follows three stages: attackers send malicious links to users → users click and load a malicious page → the page mimics a legitimate login portal to steal account credentials.
Current detection relies heavily on blacklists of confirmed malicious indicators (IoCs) such as domains, URLs, and IP addresses. Security vendors gather IoCs through multiple channels, but this requires real-world interaction — a potential victim must either fall for the attack or report suspicious behavior.
Once a malicious page is flagged, security analysts or automated tools verify the content before adding the IoC to blacklists. These are then distributed through threat intelligence feeds and integrated into Security Email Gateways (SEG), Secure Web Gateways (SWG), and other network security layers.
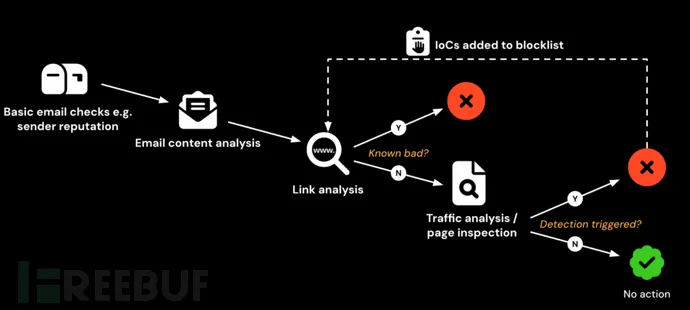
However, this system has a fundamental flaw: detecting and blocking phishing pages depends on victims encountering the attack first.
How Attackers Craft “Brand New” Phishing Campaigns
Modern attackers exploit three major weaknesses in phishing detection:
- Reliance on domain/URL/IP blacklists
- Detection deployed at email and network layers
- Requirement to access and analyze pages before blocking
These decade-old methods are now easily bypassed.
Phishing domains are highly disposable: attackers bulk-purchase domains, hijack legitimate websites, and expect domains to be eventually blacklisted. Modern phishing infrastructures dynamically rotate elements — for example, assigning unique URLs per visitor from an updated pool or using one-time magic links (making post-attack analysis impossible).
When a domain is flagged, attackers simply register a new one or compromise another trusted WordPress server — both are now widely used tactics.
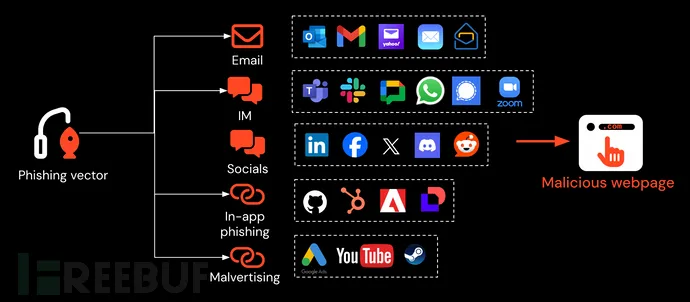
Attackers also employ cross-platform techniques: spreading links via instant messaging, social media, malicious ads, or trusted apps. For instance, sending an “innocent” PDF through social media that eventually redirects to a malicious page.
While email security systems can assess sender reputation and perform DMARC/DKIM checks, they struggle to detect the final phishing page. Even deep content analysis only spots suspicious links, and cannot tackle cross-medium attacks effectively.
Disrupting Forensic-Style Detection Models
Modern phishing pages are not static HTML but dynamic web apps rendered via JavaScript, nullifying static content detection.
To evade sandbox analysis, attackers deploy CAPTCHA challenges or bot protections like Cloudflare Turnstile. Even if these are overcome, specific URL parameters, request headers, and JavaScript execution are needed to reveal malicious content.
Furthermore, attackers obfuscate visual and DOM elements to bypass signature-based detection.
As a result, real-time phishing detection is almost non-existent. Proxy-based solutions can monitor traffic for anomalies triggered by user interaction, but reconstructing encrypted TLS traffic is complex, introducing detection delays and reliability issues.
From initial attack to IoC distribution, the timeline typically spans days or even weeks — allowing phishing campaigns to operate as “brand new” attacks. Current detection is essentially forensic (post mortem), reliant on prior identification of malicious indicators. Crucially, this means someone must have already fallen victim first.
Browser Security: The New Frontier in Phishing Defense
Endpoint security evolution offers a clue: In the late 2000s, when endpoint attacks surged, network-based detection, file signatures, and sandboxing failed to keep up. Endpoint Detection and Response (EDR) emerged, using real-time OS activity monitoring to provide effective protection.
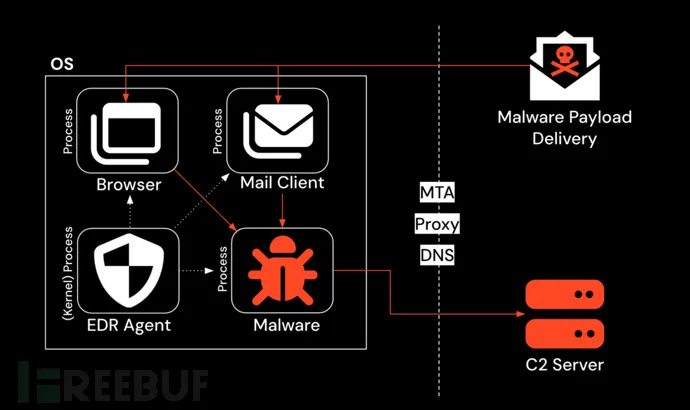
Today, we face a similar pivot point: modern phishing happens inside browser sessions, yet email, network, and even endpoint tools lack the visibility required.
The browser has become the new operating system — the primary workspace and battlefield.
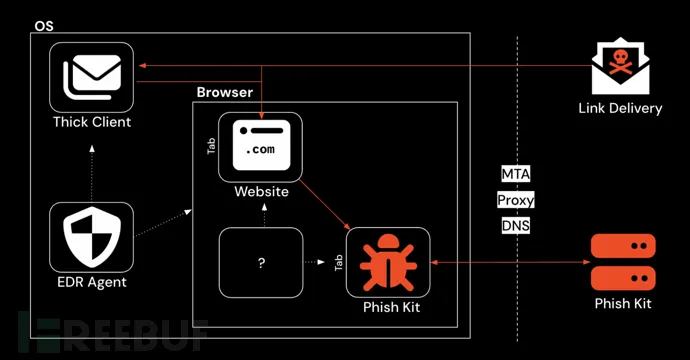
Effective protection requires real-time visibility into the webpage as users interact with it (not in a sandboxed or proxy environment). Only then can detection shift from fragile IoCs to more resilient Tactics, Techniques, and Procedures (TTP)-based methods.
Browser Extension Protection in Action
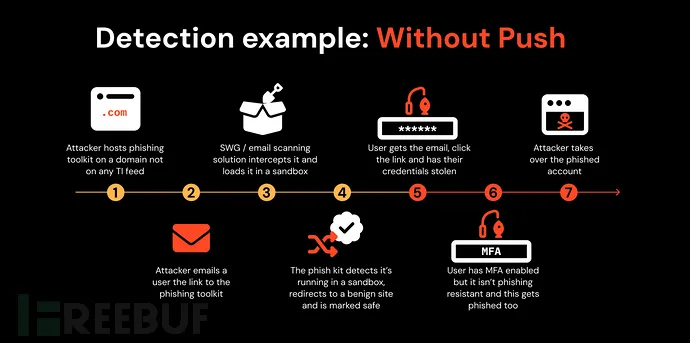
Scenario: Attackers compromise a WordPress site to host a phishing toolkit, then send emails with malicious links. Traditional SWGs or email scanners sandbox the link, but the toolkit redirects sandbox visitors to a benign page to evade detection. The real phishing page remains accessible to end users, who may enter credentials and MFA codes, resulting in account compromise.
With a browser security extension deployed, the system detects in real time:
- Password reuse across sites (indicating phishing)
- Page structure cloned from legitimate login portals
- Presence of phishing toolkits
As a result, it blocks further user interaction and cuts off the attack at the source.
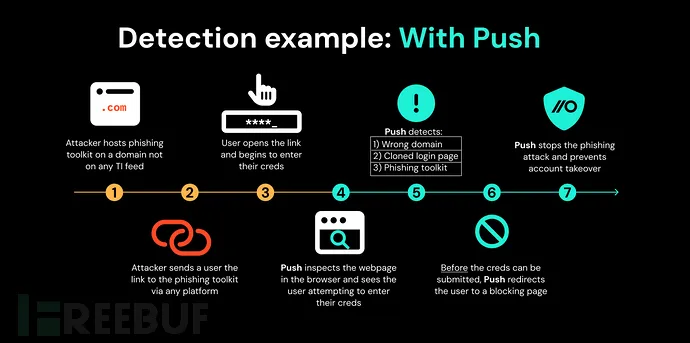
This method makes it significantly harder for attackers to succeed — when users are prevented from entering credentials into phishing pages, attacks naturally fail.